Governments around the globe are ramping up cybersecurity regulations and there’s a growing question as to what that means for the developers and users of embedded systems.
Are embedded systems uniquely vulnerable to cybersecurity attacks? Is there cybersecurity legislation that specifically covers embedded system security? And, if not, does the evolving body of cybersecurity legislation apply to embedded systems?
In this article, we’ll look at the common pain points for embedded system security, examine the US and global cybersecurity laws and regulations that attempt to address these pain points, and briefly outline what developers and users of embedded systems can do to comply with cybersecurity compliance regulations.
The Embedded Systems Security Landscape
Embedded developers operate in a vast landscape of embedded systems, tools, and methodologies in the quest to produce connected products. They come from many different disciplines, including software and hardware engineering, and bring expertise in a range of supporting knowledge areas such as communication protocols, testing and certification and more. Today, one of the fastest growing disciplines is embedded system security.
What Is an Embedded System?
An embedded system is a specialized, self-contained computer system designed to perform a specific set of tasks within a larger system or device. Embedded systems exist in applications such as consumer electronics, automotive systems, medical devices, and industrial control systems.
In industrial settings embedded systems are commonly used for tasks such as control and automation, monitoring of processes, managing equipment, and data collection and analysis. For example, in agriculture, embedded systems in irrigation systems control the timing of watering, often based on moisture sensors. And in manufacturing and supply chain applications, embedded systems control robotics, automated assemblies and pick and pack machines. Consumer technology also relies on embedded systems for automation and control; think smart home devices, wearable technology, home appliances, etc.
It’s worth noting that most IoT devices contain an embedded system, though not every embedded system is an IoT device. IoT connectivity means that the embedded system can now be monitored and managed from anywhere — but also attacked from anywhere.
Cybersecurity Risks Amplify As Embedded Systems Connect to the Internet
Like every type of technology, embedded systems are vulnerable to a unique subset of cybersecurity attack vectors, which includes hardware security flaws, and vulnerability to attack strategies such as buffer overruns, man in the middle, and denial of service.
These risks are, of course, not new. However, there’s a critical aspect that’s changed making embedded systems much more vulnerable than they used to be.
In the past embedded systems tended to function in relative isolation — operating within a device or group of devices that was linked to an internal network, but not the outside world. Today, devices that use embedded systems are increasingly connected to the Internet.
Connecting a device to the internet by turning it into an IoT device greatly amplifies the cybersecurity risks:
- Increased attack surface: Connected to the Internet, embedded systems become a part of a larger digital domain, which makes them more susceptible to attacks.
- Lack of security protocols: Slim security protocols designed for isolated devices are not sufficiently robust when the system is exposed to the Internet.
- Limited updates and patches: Updates and patches for embedded systems rarely keep up with the fast-moving nature of online threats.
- Integration with other systems: Embedded systems connected to the Internet commonly integrate with other connected systems e.g., cloud and mobile apps, which further enlarges the attack surface.
Before the IoT revolution, attackers needed to be an insider or physically break into premises to launch an attack. Today, embedded systems — with all their flaws — are exposed to a global hacking community.
Easy For Hackers to Reach — Hard For Users To Update
Embedded systems have unique security vulnerabilities but are also more difficult to keep secure than other technologies, for three key reasons:
- Product lifecycle: Unlike many other technologies, embedded systems have service lives of decades - think about aircraft, defense systems, power plants, etc. Developers have the challenge of countering a lifetime of unknown, unpredictable cybersecurity risks in the design phase.
- Difficult to update: Embedded systems can be physically hard to reach — think monitoring stations scattered across a large country, for example, or the control system embedded deep in a mine. Furthermore, it is worth bearing in mind that battery powered devices are not always powered on and reachable to deploy updates.
- Lack of flexibility: The monolithic nature of the OS in some systems and the limited memory and processing capabilities of embedded hardware also cause restrictions to the type of security defenses developers can add post market.
That said, the difficulty of updating embedded systems varies - smart TVs or smartphones can be frequently updated with little inconvenience to the end user, but industrial control systems are harder to update.
How Cybersecurity Regulation Is Responding to Threats

The difficulty of updating embedded devices sometimes makes manufacturers reluctant or unable to respond to threats. Best-of-breed manufacturers will always do what’s needed to ensure tight cybersecurity, but others will do the minimum. In other words, it’s a job for regulators.
Embedded Systems Cybersecurity Regulations
There is no regulation specific to embedded systems. Nonetheless, embedded systems are covered by cybersecurity compliance regulations by virtue of the nature and applications of the device that contains the embedded system.
For example, a medical device such as an X-ray machine containing an embedded controller could be covered by cybersecurity regulations for medical devices. Likewise, the embedded technology inside an IoT device — a connected thermometer for example — could be covered under IoT cybersecurity regulation.
We can’t comprehensively cover every cybersecurity law that applies to embedded systems, but in this section, we’ll provide an overview that outlines just how broad (and how new) much of this regulation is.
New Cybersecurity Regulations in the US

In the US, many efforts to improve cybersecurity are underway, some of which apply to devices using embedded systems. That includes laws that cover IoT security requirements, and sector-specific regulation affecting e.g., healthcare and financial services.
Take connected medical devices, for example. In 2022, the FDA Act was amended by adding a requirement for connected medical devices — including the need to monitor devices while in the market, a software bill of materials (SBOM), and time windows for patching.
The new legislation carries implications for the embedded systems integrated into connected medical devices. Similarly, in financial services, requirements around e.g., Payment Card Industry Data Security Standard (PCI-DSS) would apply to the embedded systems inside devices that handle payment card data.
Thinking about California cybersecurity regulations, California passed SB-327 covering cybersecurity and privacy in the IoT sector, including requiring manufacturers to assign unique preprogrammed passwords to each device, while the California IoT law (SB-327) also requires manufacturers to take reasonable security measures.
In terms of Federal cybersecurity regulations, the IoT Cybersecurity Improvement Act of 2020 focuses on IoT devices used by federal agencies but nonetheless indirectly impacts consumer products. Again, because IoT devices tend to contain embedded systems it means that the Act has implications for embedded technology cybersecurity.
Global Cybersecurity Regulations
EU regulation has significant reach because global manufacturers would ensure their device complies simply to sell into the EU market — which means that in effect, EU law reaches globally. In the EU, the laws that can affect embedded system cybersecurity include:
- Radio Equipment Directive (RED): Applies cybersecurity requirements to devices that contain radio equipment components, such as Bluetooth or Wi-Fi modules, regardless of whether said devices are finally interconnected or not, which again commonly go hand-in-hand with an embedded system inside devices.
- Regulations for medical devices (MDR) and in vitro diagnostic medical devices (IVDR): These regulations outline cybersecurity requirements for medical devices in the EU, including post-market surveillance, incident reporting, traceability, and testing.
- NIS2 Directive: Applies to highly critical sectors, which commonly deploy embedded systems — with a focus on the security of network and information systems.
Other acts such as the General Data Protection Regulation (GDPR) and the EU Cybersecurity Act will also have implications for embedded technology, while signs are that the Cyber Resilience Act (CRA) will cover many applications where embedded systems are commonplace.
Individual countries also apply their own laws. For example, in 2020, the Japanese Ministry of Economy, Trade and Industry (METI) announced its IoT Security and Safety Framework (IoT-SSF). The framework evaluates security measures for IoT devices and systems, as well as new risks introduced by the integration of cyberspace and physical spaces.
IoT Cybersecurity Standards Behind Legislation
It’s worth noting that some of the regulations and guidelines summarized in this section are based on existing IoT cybersecurity standards such as EN 303 645 and IEC 62443-4-2.
Therefore, it’s advisable to take broader IoT security standards into account when evaluating the design of connected embedded systems.
Particularly for products that will be shipped to Europe in 2024 and later, manufacturers should seek proof that their products meet these standards or obtain a third-party certification as needed.
As for the US, there is also the NIST Cybersecurity for IoT Program, NISTIR 8259A: Core Device Cybersecurity Capability Baseline (May 29, 2020) which should be considered by manufacturers of IoT devices.
Security Requirements for IoT Devices
We’ve outlined why embedded system cybersecurity is becoming so critical: devices with embedded technology are now commonly also IoT devices, simply because we’re living in a more connected world.
Fundamental Embedded Systems Security Requirements in IoT
Securing IoT devices and the embedded systems inside means starting off with embedded system security good practices. That includes established techniques such as:
- Root of trust which provides essential functions to enable trusted boot, cryptography, attestation and secure storage. The root of trust is used to keep private crypto keys (encrypted data) confidential and unaltered, protected by hardware mechanisms.
- Secure boot that leverages the signature provided by a device trust anchor to ensure that software running on a device is authentic and has not been tampered with.
- Executable space protection which marks specific memory regions as non-executable so that an attempt to execute machine code in those regions causes an exception.
- Stack canaries to allow the operating system to detect a stack buffer overflow before executing malicious code.
But these are fundamental embedded security design decisions; device manufacturers must also ensure that they can adapt to the changing threats of an online world throughout the lifecycle of a product and to the related compliance and regulations for cybersecurity.
Security Requirements in IoT Architecture
The rapid pace at which cybersecurity risks are evolving means that the security capabilities of devices must be managed once they’re already in the market. Strategies to meet today’s security requirements in IoT architecture include:
- Product lifecycle management: Use cloud-based monitoring and update services to ensure compliance with cybersecurity legislation at every stage of a device's lifecycle, from approval to end-of-life.
- Transparency and compliance: Maintain a comprehensive analysis to build a custom SBOM, while monitoring for vulnerabilities throughout the life of the device — allowing manufacturers to fulfill their transparency obligations by identifying critical vulnerabilities as they emerge.
- Threat response: Maintain the ability to promptly push critical updates to address any emerging vulnerabilities while the embedded system operates in the user setting.
Making these suggestions is the easy part, of course. Implementing it in the context of embedded systems is another question. It comes down to the toolset.
Digi Solutions for Embedded System Security
Developers, systems integrators and manufacturers need an integrated IoT security system that allows them to manage the security of a fleet of IoT devices across the product lifecycle: from release into the market, right to end of life.
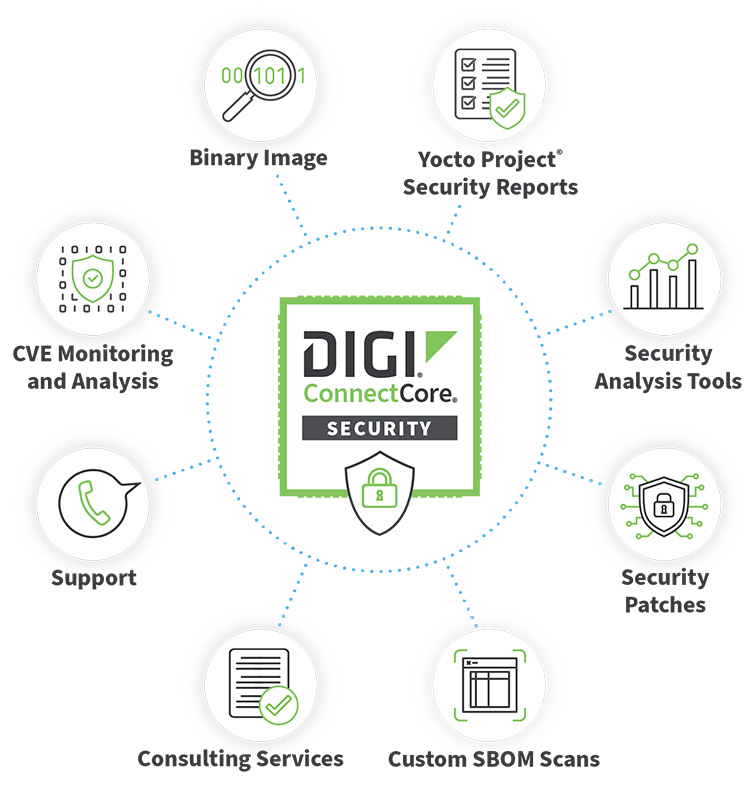
Digi supports the full lifecycle of development, testing, security integration and ongoing management with a full suite of developer building blocks — including the Digi ConnectCore family of highly integrated system-on-modules — and tools for rapid product design, wireless integration, embedded security and ongoing lifecycle management.
That includes leveraging our IoT security framework Digi TrustFence® that enables manufacturers to easily integrate device security, device identity, and data privacy capabilities into their product design. In combination with the use of services such as Digi ConnectCore® Security Services that monitor threats once the device is in service, and that enable manufacturers to integrate fixes for identified vulnerabilities, and Digi ConnectCore Cloud Services to securely publish and deploy device updates to counter new threats.
By designing for security from the outset, and ensuring active security management across the product lifecycle, OEMs building with embedded systems can comply with the growing volume of IoT and industry-specific embedded cybersecurity regulations. Digi's suite's of SOMs and developer tools and services can help you achieve these goals. And if you need engineering support to help bring your connected system through the product development cycle for rapid time-to-market and meet all of today's requirements, Digi Wireless Design Services can help.
You can find out more about how Digi’s range of management and security solutions for embedded systems can help your organization comply with cybersecurity by visiting the Digi ConnectCore Embedded Solutions page here.
Next Steps